Cybercrimes have been on a very large scale in recent years and people have lost a large amount of money and resources due to cyberattacks.
As of 2019, cyber-attacks are considered among the top five risks to global stability, and according to HealthITSecurity, over $4.2B has been lost to phishing attacks in just 2020.
Cybersecurity Ventures also reports that worldwide cybercrime costs will hit $6 trillion annually by 2021 (this year), which includes theft of personal and financial data.
Everyone is prone to a security breach, be it a phishing attack, ransomware, adware, trojans, etc. The difference between people that have been hacked and people that have not is simply just how they prevented it.
In this article, you'll learn about 3 common security threats that can negatively affect your personal devices and how you can prevent them.
📚 Prerequisites
- A willingness to learn.
- A computer/device you want to protect.
🚩 Common Cyber Attacks and Prevention Strategies
1. Phishing
Phishing is the fraudulent acquisition of personal credential information such as your username and password, and it is commonly done via mail.
Some phishing examples include:
- Spear phishing - phishing attack that targets specific employees in an organization to gain access to sensitive information.
- Whaling - phishing attack that targets top managers (i.e CFO, CEO, etc) in an organization to steal corporate information and company funds.
- Vishing - phishing in form of voice calls.
- Smishing - phishing in form of SMS.
Prevention Strategies
- Spear Phishing and Whaling
Attackers usually use social engineering principles(authority, familiarity, trust, urgency, etc) to manipulate their targets into providing sensitive information about themselves like credit card details, passwords to their accounts, etc.
Phishing attacks are usually conducted either using one or all of the social engineering principles, but oftentimes, most of the social engineering principles are used by scammers in the real world to succeed in their phish attempt.
You can prevent this by being aware of how phishing attacks are and not fall for them!
Never click on links that request your passwords or username or emails that request your credentials.
Another way to avoid them is by navigating to the main site and confirming the content of the mail you received, never click or download any file from a mail that you are not sure about.
They may look real and seem real, but if you look close enough they are not!
Luckily, phishing attacks are typically the same, and here is a real-life example.
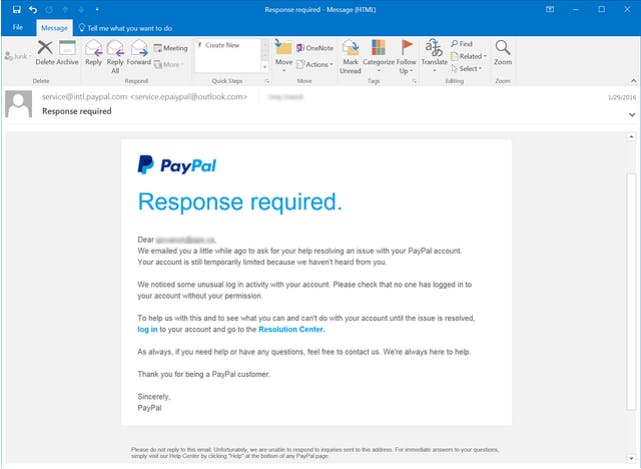 Source: www.phishing.org
Source: www.phishing.org
If you look closely at the example above, you'll notice that even though the email is present to look like PayPal's email format, one can tell it's not from Paypal by simply looking at the email address on the header (service.epaiypal... that's definitely not how Paypal is spelled) and Paypal would not ask you to reveal your financial information or your login details via a link from their mail.
For more information on identifying fake email messages (not from Paypal) click here
- Vishing and Smishing
Vishing and smishing attacks follow the same social engineering principles mentioned above, to gain access to accounts or steal funds via voice call or SMS.
Example:
Vishing attack
If a penetration tester calls claiming to be a senior leader's assistant in another part of your company (thus leading authority and possibly familiarity responses) and then insists that that senior leader has an urgent need (urgency) and informs their target that they could lose their job if they don't do something immediately (intimidation), they are more likely to be successful in many cases than if they only used one principle.
Source: CompTIA Security+ Study Guide: Exam SY0-601
For smishing, banks and payment platforms never request your details over the phone or through an SMS. Never click on a link via SMS or reply to them if you are not sure!
Here are some examples:
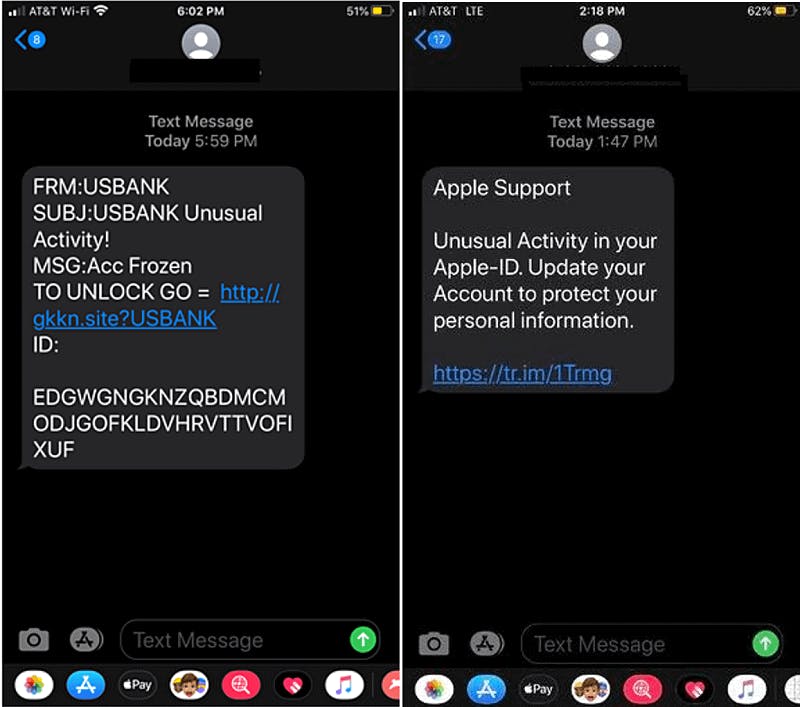
Source: purplesec.us
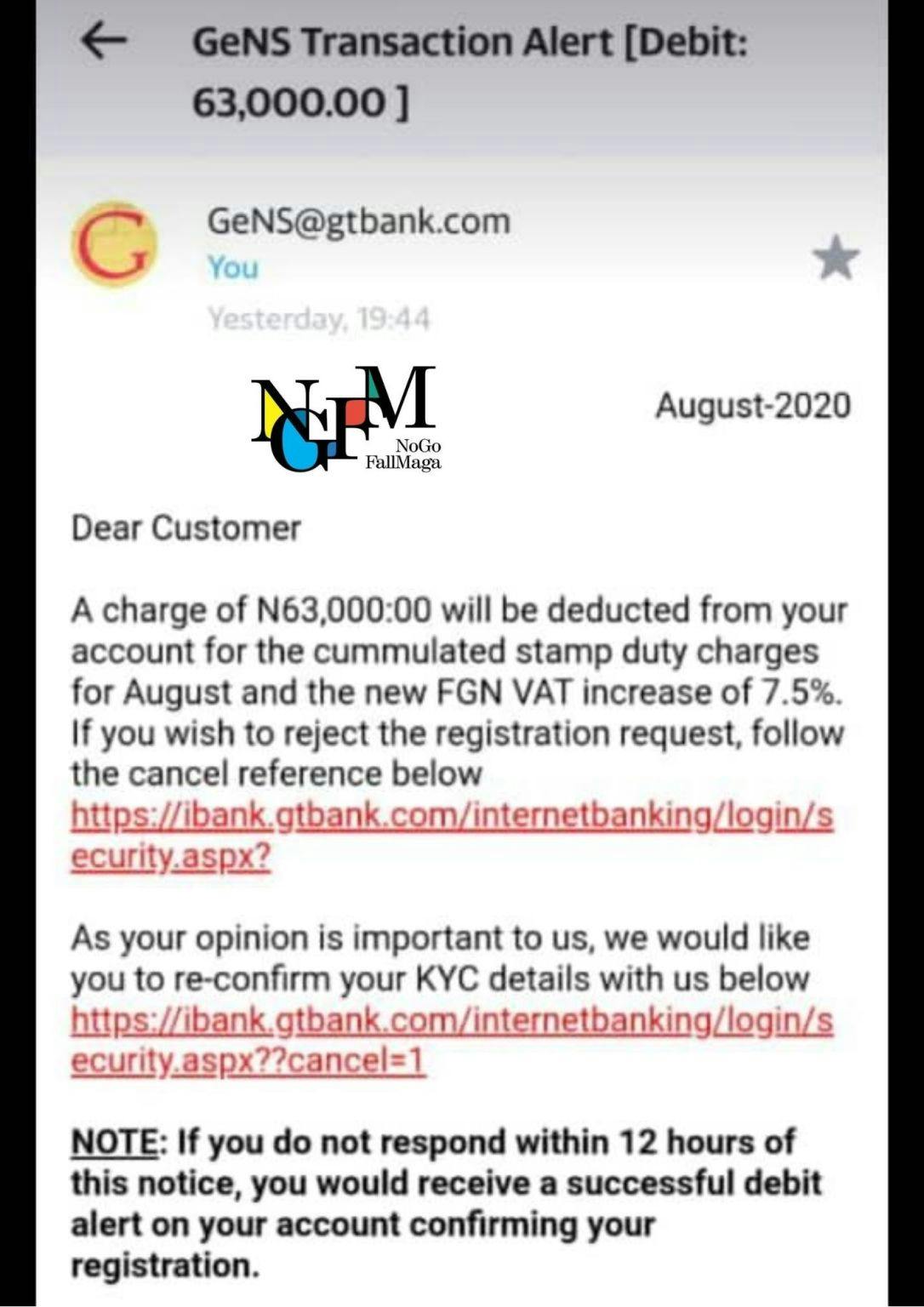 Source: cybersafefoundation
Source: cybersafefoundation
As you've seen above, there is usually a link sent to you to click on, sometimes through typosquatting like the link shown above (https://ibank.gtbank.com/...) which is not the REAL gtbank domain name (its real domain name doesn't start with 'ibank'), and scammers might even make the fake website look so real that if you aren't careful enough, you might fall for their schemes.
Prevention Strategies
- Again, don't click on the link or reply to the sender.
- If you are not sure about its legitimacy, contact your bank or that particular service provider from your browser.
2. Password Attacks
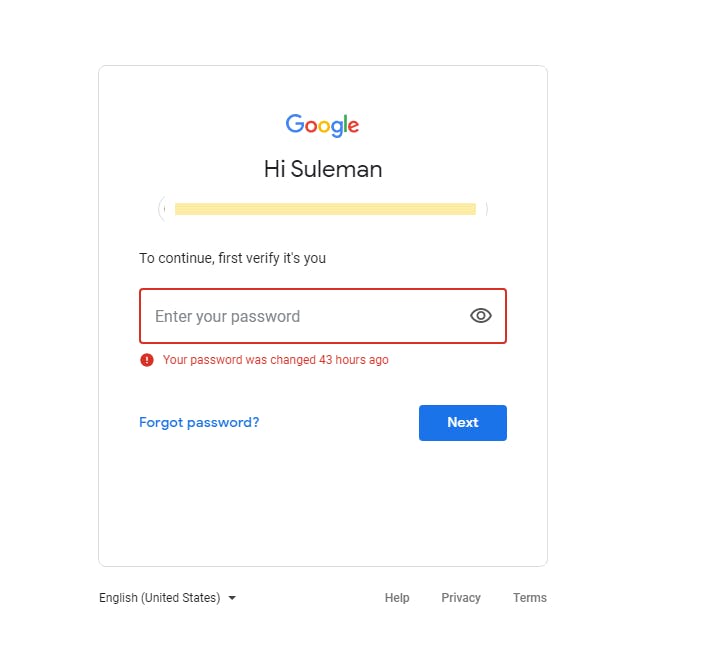
Imagine trying to login into your google account and it tells you this:
"Your password has been changed 43 hours ago"
However, you weren't the one who changed it, somebody else did.
In other words, you've been hacked! And now, the hacker has access to everything linked to that email address or used by it, including emails that contain sensitive information.
And no, I'm not trying to strike fear in you, I'm just trying to alert you of the dangers of not properly securing your devices and emails.
To prevent this, you can take any of the steps listed below, however, I'd advise you to take as many as you can to further prevent yourself from being hacked.
Enable MFA (Multi-factor authentication) which is an authentication method whereby you are only given access to an account or service, once you provide 2 or more pieces of evidence to an authentication mechanism, and depending on the service you're using, technologies like Gmail allow you to enable it via the settings option see this post for more info.
Have a strong password - A good email or website that requests sign-up details would ask for your password to be a mixture of alphanumeric and symbol characters to make guessing your password harder. However, because of the complexity and difficulty in remembering a strong password, NIST suggests that the single most important in ensuring strong password formulation is the length and requiring nothing else (i.e ILoveSunkanmisBlog > Qwerty123#).
Don't use generic passwords - Cybernews' 2021 most commonly used passwords contains a list of commonly used passwords in recent times, best to avoid using these for places where you have sensitive information as hackers can use these to gain access to your account.
Have multiple passwords for different accounts - Password spraying (a form of brute force attack) attempts to use a single password or a small set of passwords for multiple accounts. Simply put, if you only have one password cut across multiple accounts, your other accounts are most likely to be hacked as well.
If you're worried that you won't remember all your passwords, try storing them in a password vault like keypass, 1Password, etc. It'd help to keep it organized and in one place.
3. Malware
Malware is any software intentionally designed to damage a computer, server, client, or computer network.
And there are different classifications of malware as it is also a broad term used to describe a wide range of malicious software, some of which include:
Ransomware - Malware that takes over your computer system by encryption and demands a ransom.
Trojans - Type of malware typically designed as legitimate software.
Keyloggers - Programs that capture keystrokes from keyboards.
Viruses - Malicious programs that self-copy and self-replicate, etc.
Prevention Strategies
If you don't want malware silently installed on your system, then
Stop visiting illegal sites to download games or watch movies, I mean some sites even ask you to "disable your antivirus" for software to install or movie to open. That itself is a red flag 🚩.
You don't know whatever it is you're installing after the fact, and some malware that we've seen above can act like legitimate software, meaning you can be running trojans without ever noticing!Download and install a good antivirus software as this can help protect you from viruses and their transmissions, help you block ads and spam, abort connections from malicious sites, increase performance, and much more.
If you'd like to install free antivirus software, check out pcmag's 2021 best free antivirus picks.Regular security patches from your OS and software updates can also help prevent malware from being installed on your device as software providers discover and fix vulnerabilities and bug issues that can be exploited by cyber attacks.
✍🏾 Conclusion
As we've read above, cyber attacks can come in different forms, and how threat actors can manipulate us into providing credit card details and other sensitive information.
Knowing how scammers and cybercriminals work, and the ability to spot and avoid a scam or malware can save you money, time, and resources.
Disclaimer: This article was written to inform you of ways to protect your personal devices, if you want protection on all your endpoints in the network of your organization or you want to know how they can be protected, feel free to contact me via my email sunkanmifafowora@gmail.com
Don't let it happen to you before you take action or remediate it, prevention is better than cure, or as Benjamin Franklin would put it:
"An ounce of prevention is worth a pound of cure."
~ Benjamin Franklin
I'd like to thank two of my mentors in cybersecurity, Lekan Ajani and Chuks Okonkwo for their useful feedback and inputs on this article! You're the best!
If you have any questions you want to ask in the comment section or you want to like this post, join Hashnode today using this link to do so!
Thank you for reading! Remember to educate someone else about this! 💛